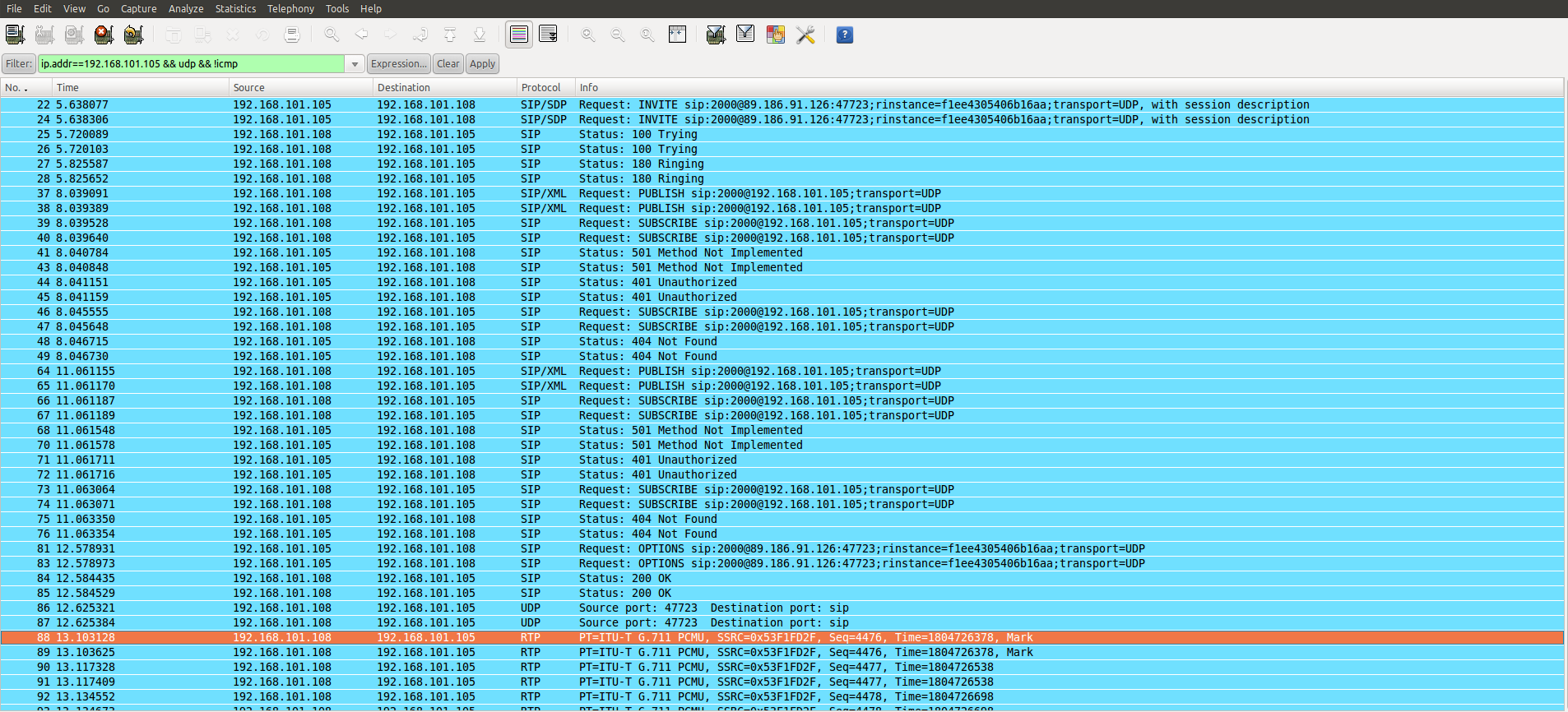
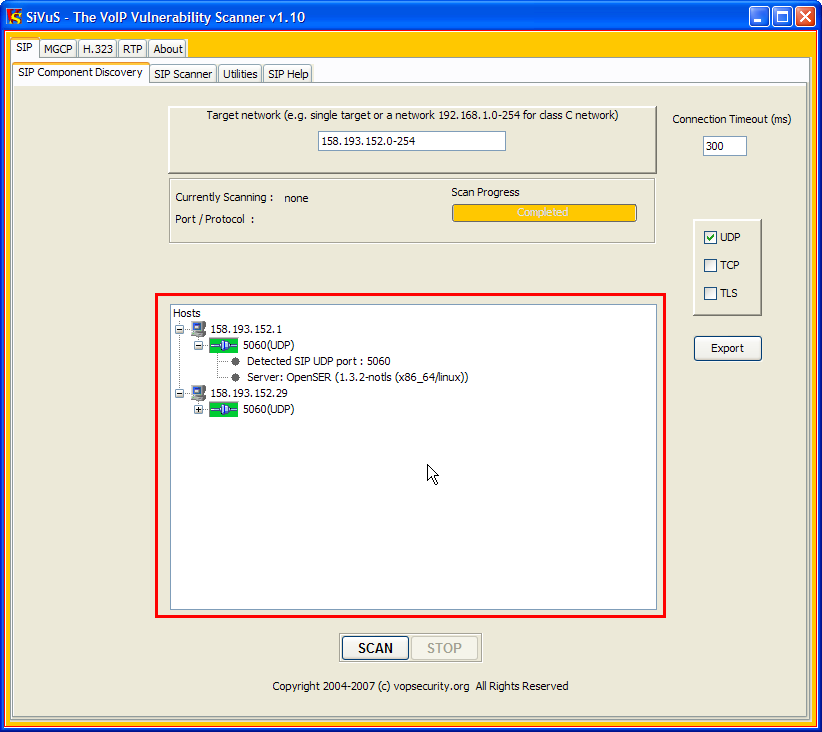
Bad Packets on Twitter: "What is @ANSSI_FR scanning for? @spiderfoot users can query for 92.154.95.236 to receive the full list of Bad Packets® CTI tags. https://t.co/hot4sEpdMs" / Twitter
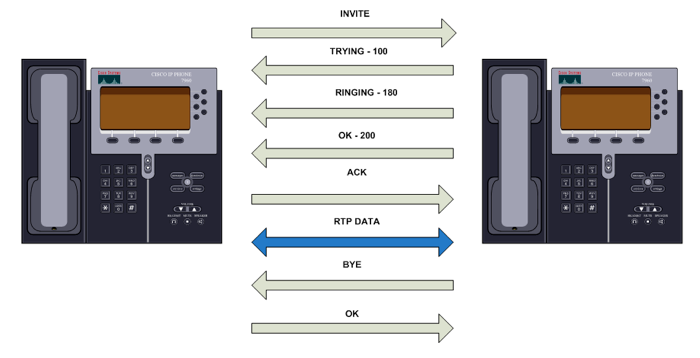
SIPVicious (Auditing SIP Based VoIP System) :: Tools - ToolWar | Information Security (InfoSec) Tools










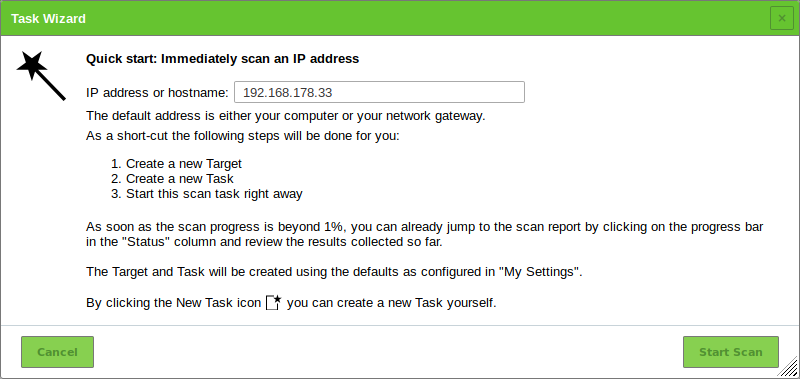
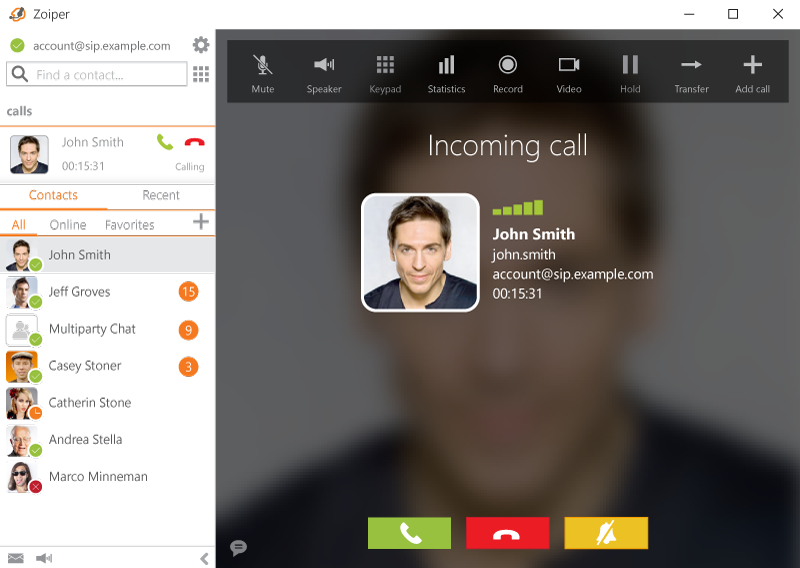



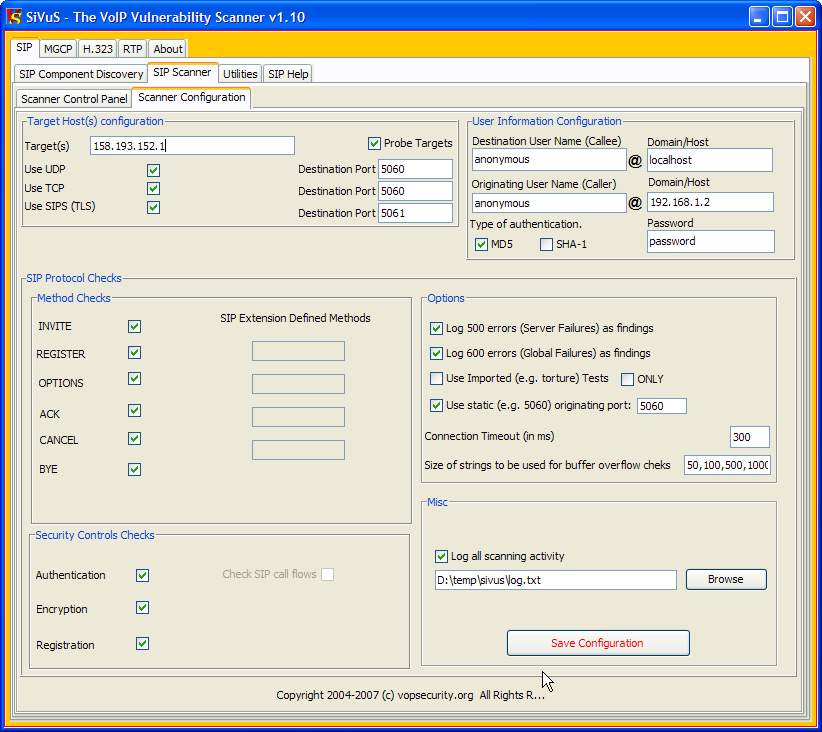

.png)